The following article presents an overview about the emerging technology of wireless broadband networks. It focuses on the history, equipment, standards and implementation of Wi-Fi networks. The main objective of this research paper is to understand the various problems associated with the implementation of these WLANs and propose recommendation and measures to solve these problems and minimize the potential risks.
Introduction
Telecommunication has become an integral part of our daily lives and is widely contributing to advancement in various fields. One of the emerging modes is wireless broadband technology which transmits multiplexed information over a wide band of frequencies. The deployment of wireless broadband services is done by weighing the geographical population density against bandwidth limitation. Wireless technologies are designed to reduce the time and different types of constraints created by cables and are more convenient than wired networking. In 1997, ‘Wireless Fidelity-popularly known as Wi-Fi technology was developed by the IEEE 802.11 standards, which provided users the freedom to connect to the internet from any location. But this service was very expensive until 2002, however the new 802.11g standards in 2003 have made WiFi enabled devices available to the masses, resulting in a Wi-Fi router becoming a household item in most modern homes in India today.
Since its inception, Wi-Fi technology has come a long way in providing quick wireless access to internet applications by transmitting data across a radio network, making the access process faster than traditional modems. Radio bands such as 2.4GHz and 5GHz depend on wireless hardware such as Ethernet protocols for Wi-Fi technology and CSMA enabled devices such as laptops, mobiles, tablets, etc. Many organizations and users have found that wireless communication and devices are convenient, flexible and easy to use. Users of wireless local area network (WLAN) devices have the flexibility to move their laptop computers from one location to another while maintaining connectivity with the network. Wireless personal networks allow users to share data and applications with network systems and other users, without being tied down by printer cables and other peripheral device connections. Users of handheld devices such as personal digital assistants (PDAs) and cell phones can synchronize data between PDAs and personal computers and use network services such as wireless email, web browsing, and Internet access. In addition, wireless communication can help organizations cut down on their wiring costs.
A. WiFi – Software Tools
Windowusers: knsgem2, NetStumbler, Omnipeek, Stumbverter, Wifi Hopper, Aptools.
Unix users: AirCrack, AirCrack-PTW, AirSnort, Cowpatty, Karma. Mac users: MacStumble, Kismac, Kismet.
(Users can select a Wi-Fi software tool that is compatible with their computer or else it must be built in)
B. To connect to Wi-Fi
A wireless adapter card is required. SSID infrastructure, and data encryption are also required.
Wi-Fi security methods include -MAC ID filtering, static IP addressing, and WEP encryption.
C. Wi-Fi network technology is based on the IEEE 802.11 protocol. As per the different Wi-Fi standards:
1) 802.11A technology has a range of 5.725 GHz to 5.850GHz with a data rate of 54Mbps.
2) 802.11b with a data rate of 11Mbps at 2.4GHz
3) 802.11E addresses QOS issues and is excellent for quality streaming of video, audio, and voice channels.
4) 802.11F addresses multivendor interoperability.
5) 802.11g deals with high data rate extensions in 2.4GHz to 54Mbps.
6) 802.11h deals with dynamic frequency selection and transmit power control for operating 5GHz products.
7) 802.11i addresses enhanced security issues.
8) 802.11J addresses channelization in Japan’s 4.9GHz band.
9) 802.11k enables the medium and network resources to be used more efficiently.
10) 802.11 deals with wireless network management which is still a work in progress.
Existing Technologies and Problems
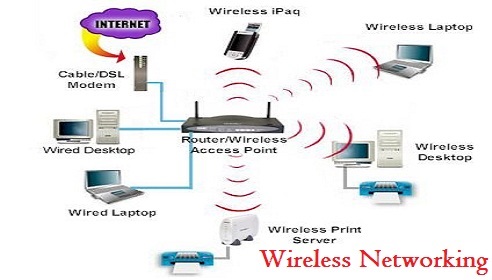
The basic existing technology for implementation of wireless networks (WLAN) in residential and enterprise setups can be understood from these explanatory diagrams alone.
However our major concern in this research paper is that there are many issues associated with the deployment and management of WLAN. These include scalability, provisioning, real-time and non-real time data flow, accessibility range, power management interference from other systems operating in the same spectrum such as Bluetooth. The major problems that we need to address are- 1.Security Management 2.QOS (Quality of Service) and centralized management of WLAN.
Risk Environment
While wireless networks are exposed to many of the same risks as wired networks, they are also vulnerable to additional risks. Wireless networks transmit data via radio frequencies, and unless protected, are open to intruders. Intruders exploit this openness to access systems, destroy or steal data, and launch attacks that consume network bandwidth and deny service to authorized users. Another risk is the theft of the small and portable devices themselves.
Wireless networks and handheld devices are vulnerable to many of the same threats as traditional wired networks. Intruders who gain access to information systems via wireless communications can bypass firewall protection. Once they access systems, intruders can launch denial of service attacks, steal identities, violate the privacy of legitimate users, insert viruses or malicious code, and disable operations. Sensitive information transmitted between two wireless devices can be intercepted and disclosed if not protected by strong encryption. Handheld devices, which are easily stolen, can reveal sensitive information.
Solutions Based on Research
Recommendations for Secure Wireless Networks
• Maintain a complete understanding of the topology of the wireless network. • Keep an inventory of labeled and fielded wireless and handheld devices. • Frequently create backups of data. • Perform periodic security testing, audits, and evaluations of the wireless network. • Perform a risk assessment, develop a security policy, and determine security requirements before purchasing wireless technologies. • Carefully implement security management practices and controls to maintain and operate a secure wireless network after installation • The information system security policy should directly address the use of 802.11, Bluetooth, and other wireless technologies. • Configuration/change control and management practices should ensure that all devices have the latest software release, including security feature enhancements and patches for discovered vulnerabilities. • Standardized configurations should be employed to reflect the security policy, and to ensure consistency of operation and changes to default values. • Security training is essential to increase awareness of the threats and vulnerabilities inherent in the use of wireless technologies. • Strong cryptography is essential to protect data transmitted over the radio channel, and theft of equipment is a major concern • Enable, use, and regularly test built-in security features, such as authentication and encryption methods available in wireless technologies. • Firewalls and other appropriate security mechanisms should also be employed.
Conclusion
Organizations and individuals benefit when they protect wireless networks and devices. After assessing the risks associated with wireless technologies, organizations can mitigate the risks by implementing countermeasures to address specific threats and vulnerabilities. These countermeasures include management, operational, and technical controls that will not prevent all penetrations and adverse events, they can be effective in reducing many of the common risks associated with wireless technology.
Read Also:
- Overview Of Wi-Fi Technology
- Wi-Fi And Hotspots: Emerging WLAN Technology In Indian Context
- Negative Impacts Of Science And Technology
- Benefits Of Science And Technology
- General Architecture Of Wireless Technology